Here, each job offer is carefully reviewed to ensure a successful job search experience.
We also offer technical tests on over 100 tech topics.
Come challenge your skills in the languages of your choice, share and measure your scores with the community!Enjoy over 80 tests on various technologies with levels ranging from beginner to expert.More than 3300 interview questions available!
WeLoveDevs.com is for all IT professionals: whether you're a young developer, devops expert, or senior product owner.
Permanent contracts, freelance, internships or work-study contracts.
Permanent contracts, freelance, internships or work-study contracts.
Does it work?
Since 2016, we have assisted over 60,000 tech profiles
We have come a long way, and here are some numbers to prove it!80 000Registered profiles
3000Companies
60 000Ads read each month
50 000MCQ questions answered each month
We provide you with all the keys to better understand the companies that interest you through pages that showcase their tech stack, their tech environment, and above all, their teams.
We meet IT services and the people who are pushing the boundaries
See all
Ready? Take control of your career in 3 steps.
1. Create your express profile in 2 minutes
Introduce yourself through a quick profile to receive your first professional opportunities and apply with just one click.
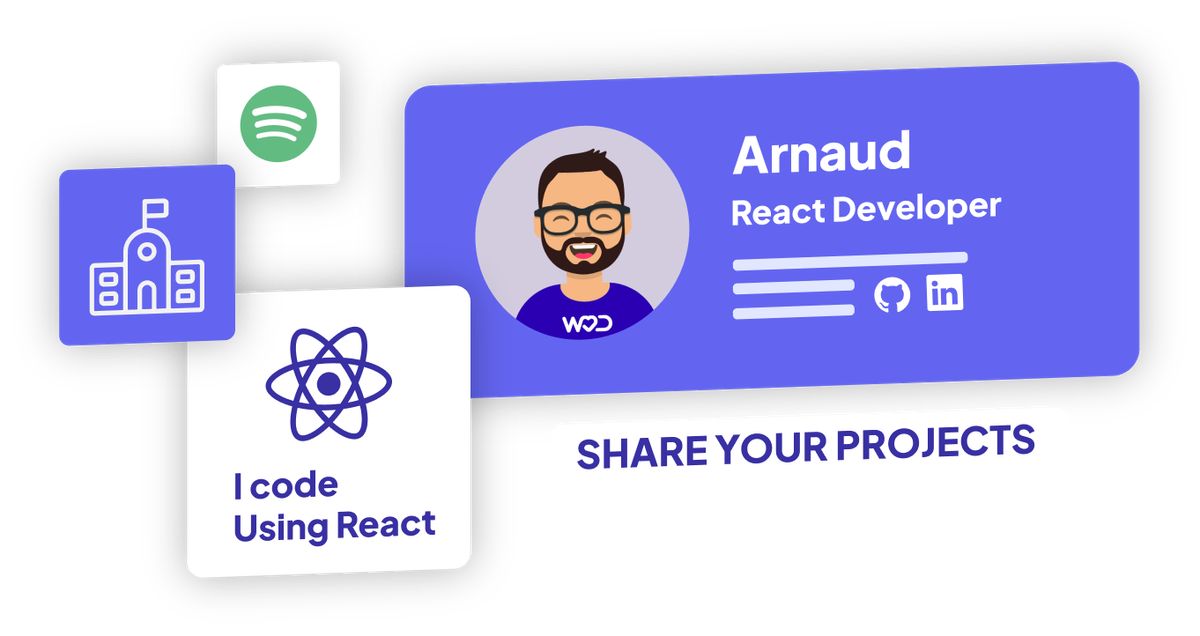
2. Boost your visibility with our comprehensive open-source profile
Do you want to find your dream job? Complete your profile with your most successful tests, your experiences, your passions...3. Control your visibility
You can choose the companies that won't be able to see you on WeLoveDevs.com. You only reveal your contact information to the companies that interest you.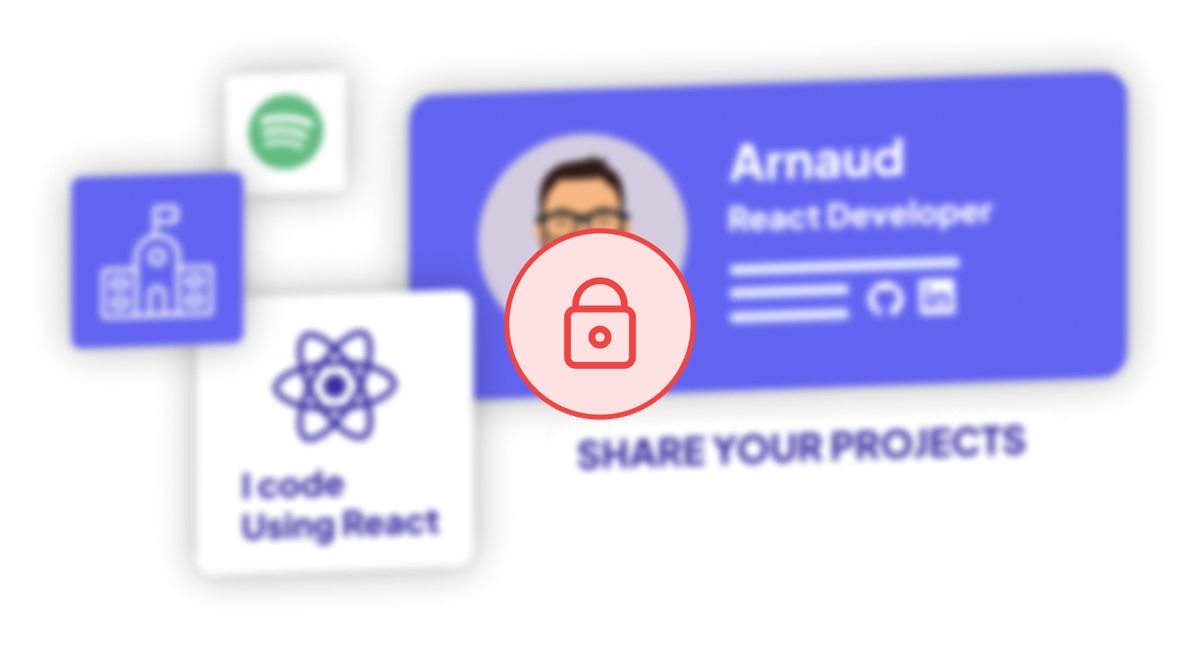
Want to go further? Discover our candidate training courses
See all
Developer testimonials
WeLoveDevs is a good way to get in touch with companies, the people working there are attentive and there are answers to questions. Highly reccomended
JérémyIT Architect
WeLoveDevs is an excellent platform for connecting with companies. I highly recommend for anyone who is open to new opportunities or juniors looking for their first permanent contracts.
SébastienAngular Developer
Awesome dev-company networking plateform ! Creating a WeLoveDevsProfile is without comparison with their competitors, give it a try !
SarahFront-end apprenticeship developer









